Configuring your Identity Provider
Partners must be aware of the following requirements and limitations for IdPs serving as identity sources for meshStack.
Supported Federation Technologies
The main supported technologies for Identity Federation with meshStack are
- LDAP
- Open ID Connect
- SAML
- Microsoft Entra ID
meshStack supports the simultaneous integration of multiple Enterprise Identity Providers (IdPs) at the Identity Broker. This allows Partners to combine identities from different sources in the platform and unify management of multi-cloud access in meshStack.
User Attribute Requirements
- IdPs must provide
- a stable and immutable user identifier (e.g. an OIDC
subclaim) - a human-readable, unique username*
- an email address
- an
euidwhen using externally-provisioned identities
- a stable and immutable user identifier (e.g. an OIDC
- IdPs should provide name (first name, given name) information to improve user experience
* Please note that meshStack currently only offers limited support for propagation of changed usernames from IdPs.
Identity Provider Configuration Tutorials
Active Directory Federation Services (AD FS)
Initially provide the URL of your AD FS to meshcloud, so a Identity Provider can be configured in the meshIdB. meshcloud will then provide a SAML descriptor URL, that can be used to configure AD FS.
With AD FS 3.0 (2012 R2) and newer, a Relying Party Trust must be created in AD FS. As OIDC Support is limited in AD FS 3.0, SAML should be used in that case and is described here. For newer AD FS versions you may also define an OIDC client, which is not part of this documentation.
In AD FS Management console, right-click "Trust relationships → Relying Party Trusts" and select "Add Relying Party Trust" from the menu. At the beginning of the wizard, enter the SAML descriptor URL that will be provided by meshcloud (it is individual per meshcloud installation) into the Federation metadata address field. Let AD FS import the settings. Proceed with the wizard, and adjust the settings where appropriate. Here we use only the default settings. Note that you will need to edit the claim rules so when asked to do so at the last page of the wizard, you can leave the checkbox checked on.
Now the SAML protocol would proceed correctly, AD FS would be able to correctly authenticate the users according to requests from Keycloak, but the requested name ID format is not yet recognized and SAML response would not contain any additional information like e-mail. It is hence necessary to map claims from AD user details into SAML document. We will set up three rules: one for mapping user ID, second for mapping standard user attributes, and optionally third for a user group, if needed.
Rule for Mapping user ID
- Open the
Edit Claim Rulesdialog. - In the
Add Transform Claim Ruledialog, selectTransform an incoming claim. - Map the following attributes:
Name IDasrule nameWindows account namefor propertyIncoming claim typeName IDfor propertyOutgoing claim typeWindows qualified Domain Namefor propertyOutgoing name ID format
- Click Finish to add the rule.
Rule for Mapping the Attributes of the Standard User
- Open the
Edit Claim Rulesdialog. - In the
Add Transform Claim Ruledialog, selectSend LDAP attributes as Claims rule. - Map the following attributes:
E-Mail-AddressestoE-Mail AddressSAM-Account-NametoSubject Name- Your LDAP attributes for
surnameandgiven name
Rule for Mapping AD groups
If meshcloud shall restrict access via certain AD groups, you can define another claim.
- Start again in the
Edit Claim Rulesdialog. - Select
Send Group Membership as a Claimrule type. - Usually two groups should be defined via this. They should result in Outgoing claim type
Groupwith Outgoing claim valuesmeshUserandmeshManager. AmeshUsercan login to meshcloud and be invited to existing meshWorkspaces. AmeshManageris allowed to create newmeshWorkspaces.
Microsoft Entra ID
To set up Entra ID for IDP authentication follow these steps:
-
Create a new non-gallery Enterprise Application in Entra ID (Microsoft Documentation) with display name
meshcloud SSOor similar.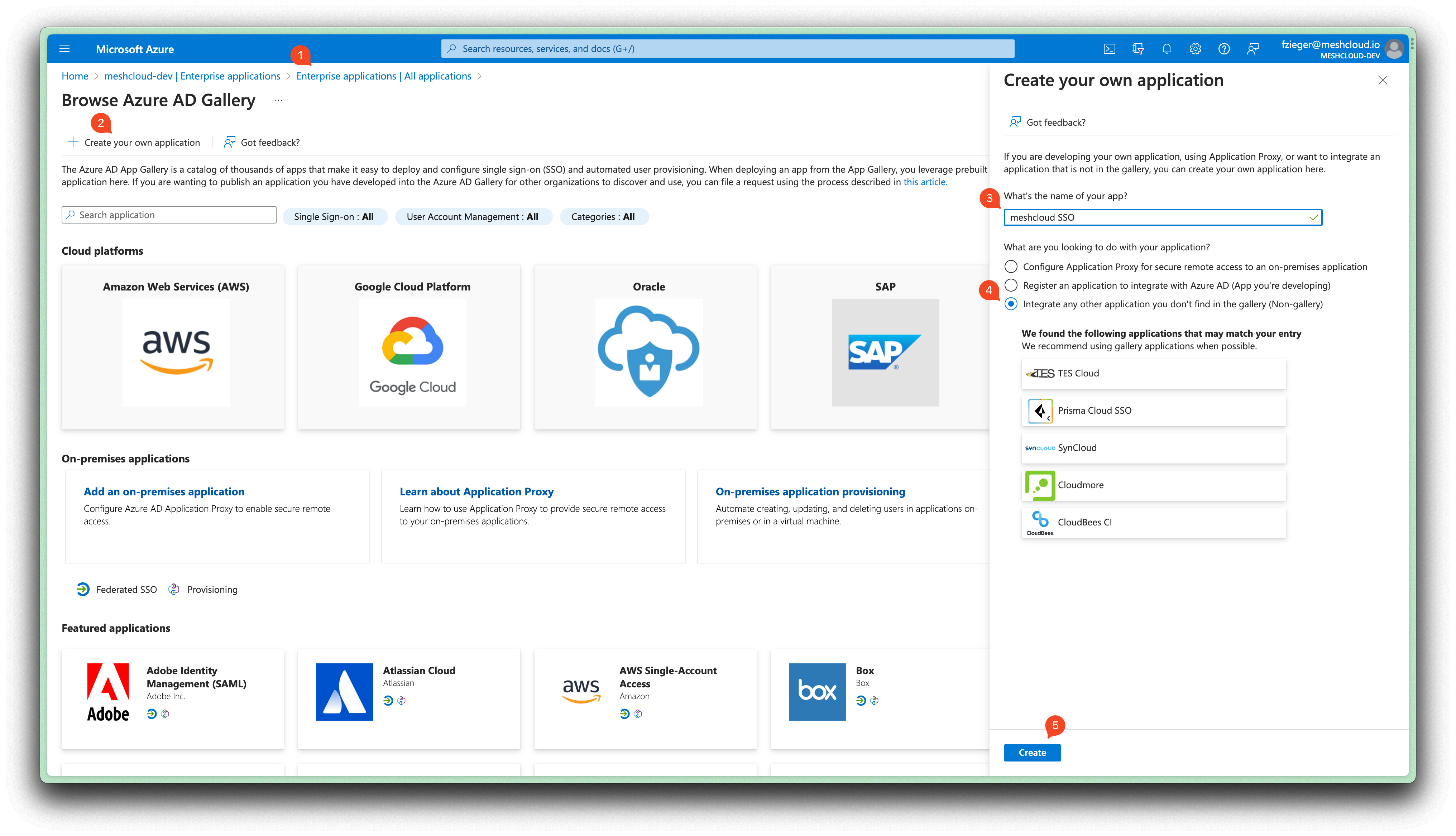
We create a non-gallery Enterprise Application (that creates an App Registration) instead of directly creating an App Registration here because provisioning via SCIM will be set up later with this Enterprise Application.
-
Open the App Registration for
meshcloud SSO. Navigate to Authentication and add a new Platform of Type Web. Enter the redirect URI for your meshStack that was provided by meshcloud.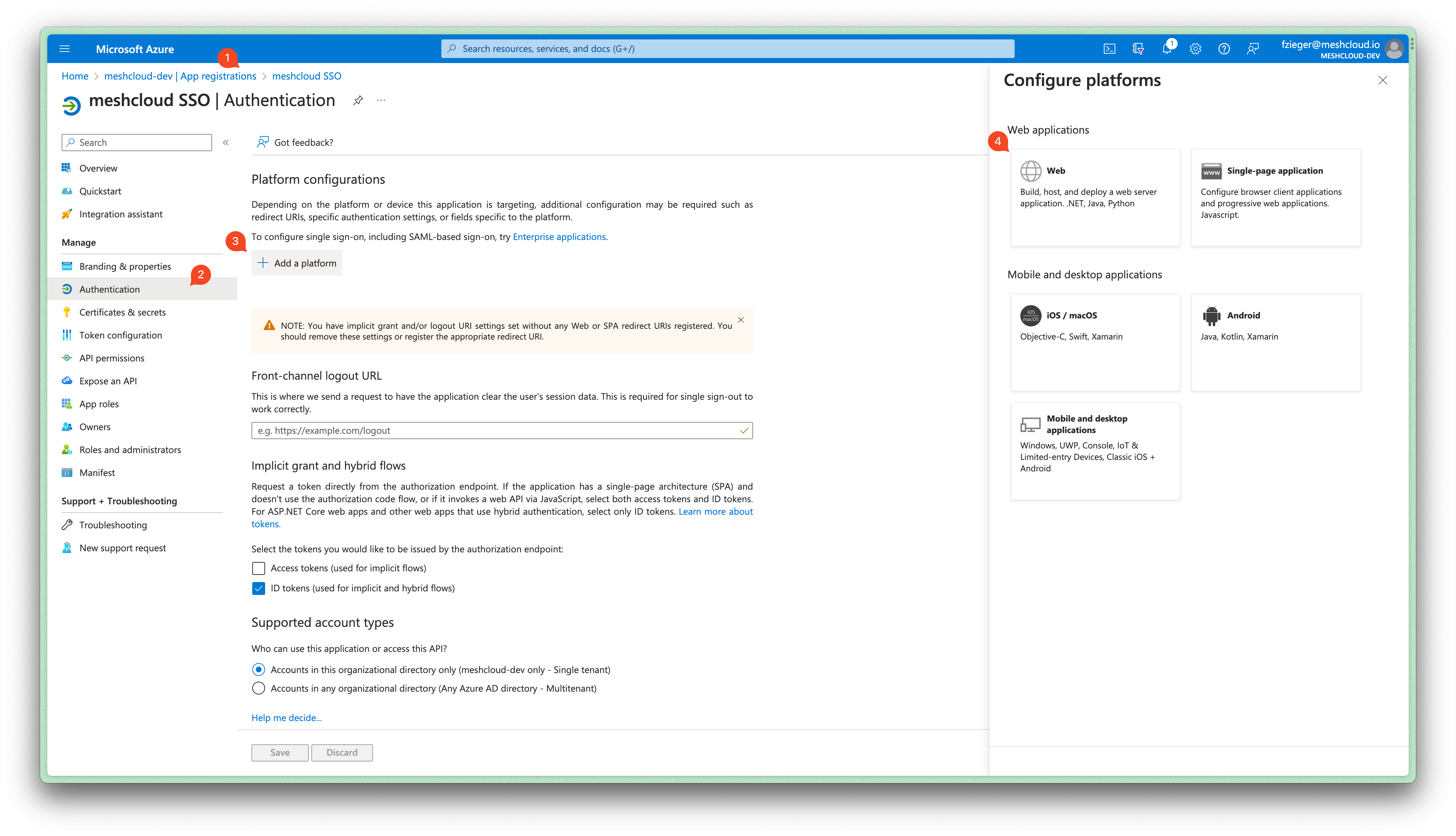
-
Create a client secret via "Manage -> Certficates & Secrets". This secret must be shared with meshcloud.
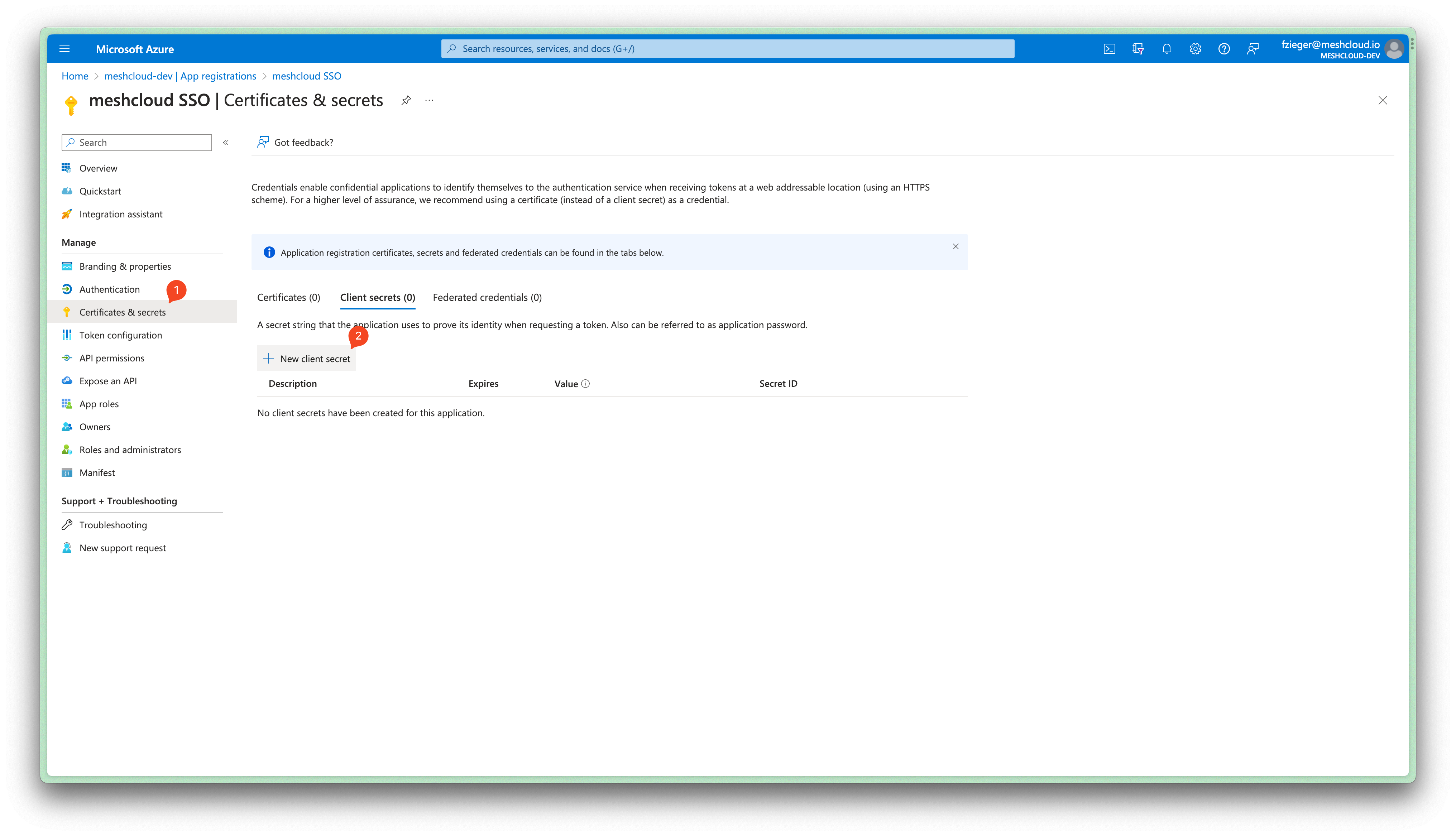
-
Share "Application (client) ID" and "Directory (tenant) ID", that is shown in the Overview screen of your new app registration, with meshcloud.
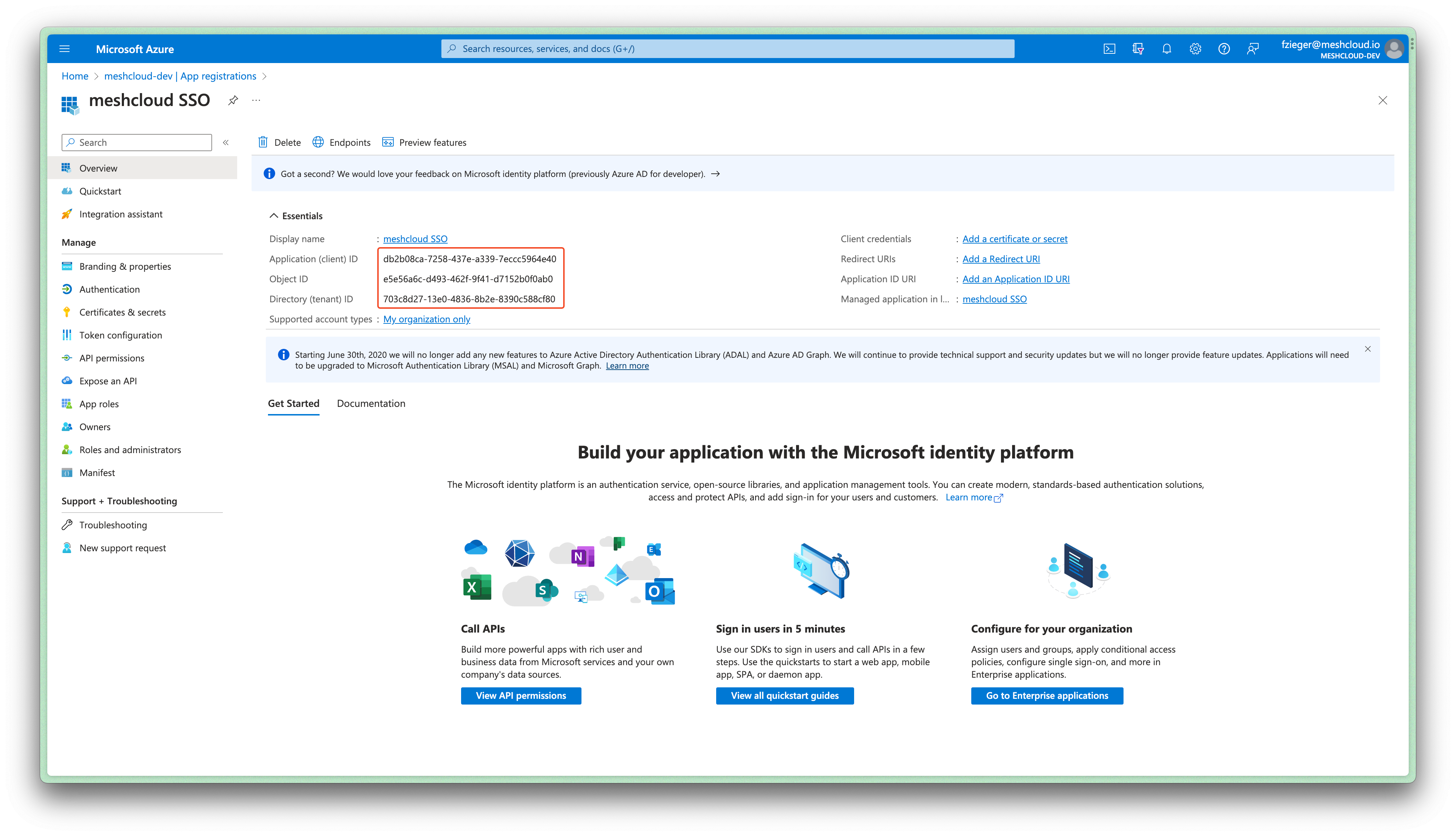
-
Provide the OpenID Connect scopes: email, openid, and profile. These scopes allow meshStack to access the user's primary email address, unique identifier, and basic profile information such as given name and surname. This information is included in the token and eliminates the need to request broader Microsoft Graph permissions like
User.ReadorUser.Read.All.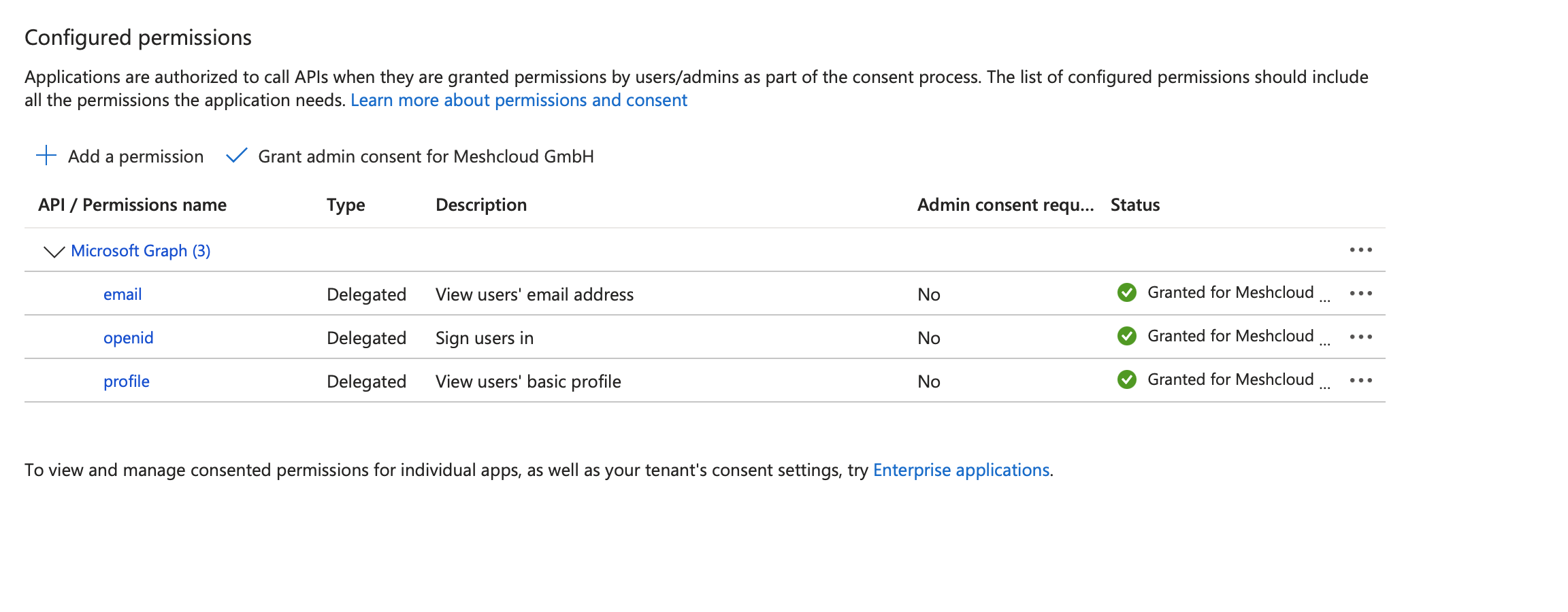
Google Cloud Directory (GCD)
The setup of the GCD Federation is quite straight forward. The easiest way to do is to setup a SAML login federation between meshstack and Google. To do so follow these steps (for more detailed steps you can also follow the SAML guide from Google):
- Login into the GCD Admin area (admin.google.com).
- Click on
SAML Appsand create a new SAML app by clicking on the plus button bottom right, thenSetup my own custom app - In the upcoming windows please download the IDP metadata. This data is important for setting up the Keycloak. Also copy the
SSO URLand provide both to meshcloud. - Chose a name (e.g.
meshstack sso), a picture and description as you like. - You probably need to input first a placeholder for the
ACS URLandEntity ID, as meshcloud can only provide you these values when we setup the SSO with the data you gathered in the earlier steps. When this was done and we notified you about the correctACS URLandEntity IDyou can edit this SAML App again and finalize its setup with the information we provided you.
You must also add three mappers so essential user information to identify the user is transferred to meshcloud during the SAML handshake. The attribute name must match exactly. The attributes are:
| Attribute Name | Source Property |
|---|---|
| Basic Information -> Primary Email | |
| firstName | Basic Information -> First Name |
| lastName | Basic Information -> Last Name |